
Is Your Old Computer a Security Risk? When to Upgrade
Is Your Old Computer a Security Risk? When to Upgrade Using an old computer can present significant security risks that many people are unaware of.
Our Data Security category provides tips and resources for protecting sensitive data, including choosing the right security software and hardware, developing effective security policies, and complying with data protection regulations. We also cover malware, viruses, identity theft, phishing, and social engineering to help our readers stay protected. Our comprehensive view of data security enables you to make informed decisions and keep your data safe. Join our community and share your experiences in the comments section.


Is Your Old Computer a Security Risk? When to Upgrade Using an old computer can present significant security risks that many people are unaware of.

Identity theft is a serious crime that affects millions of people each year. As an individual, it is important to be vigilant and watch out

Caution: The Dangers of Clicking on Links in Emails Introduction Email is one of the most common ways cybercriminals try to infect computers or steal

Data Breaches Are on the Rise – How to Protect Yourself Data breaches have unfortunately become increasingly common in recent years. As cybercriminals get more

Does Your Antivirus Software Really Protect You? Having an antivirus software installed on your computer used to be considered essential for basic protection against malware

Could Quantum Computing Pose a Threat to Data Security? Introduction Quantum computing is an exciting new field of research that leverages the properties of quantum

How to Recognize and Avoid Phishing Emails What is Phishing? Phishing is a type of cyber attack where criminals send fraudulent emails that appear to

Securing Your Online Accounts With Two-Factor Authentication What is Two-Factor Authentication? Two-factor authentication (2FA) is an extra layer of security that requires users to provide

6 Data Security Best Practices You Should Follow Right Now Data security is more important now than ever before. As cyber threats become more sophisticated,
How Encryption Can Protect Your Personal Information Encryption is a powerful tool that can help keep your personal information private and secure. Here’s an in-depth

3 Ways Hackers Will Try to Steal Your Data This Year 1. Phishing Attacks Phishing is one of the most common ways hackers try to

In the modern digital age, cloud computing has become ubiquitous. As more and more data is stored in the cloud, data security has become a

In today’s interconnected world, it is essential for consumers to remain vigilant against the ever-evolving tactics of scammers. Unfortunately, one scam that has been on

In today’s interconnected world, the risk of computer threats is ever-present. From malicious software and phishing attacks to password breaches and Wi-Fi vulnerabilities, it is

In today’s interconnected world, the invasion of harmful software into our computers poses a significant threat. These malevolent programs can disrupt our online experiences, compromise

In today’s digital age, email scams have become an all too common occurrence. With the increasing frequency and sophistication of these attacks, it has become

In today’s digital age, ransomware attacks have become an increasingly common threat to individuals and organizations alike. These malicious attacks can cause significant damage by

In today’s digital age, passwords are the keys to our online lives. They not only protect sensitive information but also give us control over our

In today’s digital age, online privacy has become a prime concern for most of us. We strive to safeguard our personal information from cybercriminals and

We all know how important our mobile devices are to us. They hold our most precious memories, keep us connected with loved ones and help

As technology continues to advance, so do the potential threats that come with it. Software updates and patches are crucial for ensuring the security of

In today’s digital age, cyber-attacks are becoming increasingly common and sophisticated. From ransomware to phishing scams, businesses of all sizes are vulnerable to online threats

As technology continues to advance, so do the methods used by cybercriminals. In recent years we have seen a wide range of cyberattacks that have

In today’s digital age, it is becoming increasingly important to protect your personal information online. With the rise of social media and e-commerce sites, we
Data recovery from damaged partitions is an essential part of digital data management. Recovering lost or inaccessible data from a damaged partition has become increasingly

Data recovery from corrupted files is a complex and often daunting process. Files can become corrupted due to various sources, such as malicious software, hardware

RAID data recovery is a complex process that requires knowledge and expertise to be completed successfully. With the right approach, RAID arrays can be recovered
Malware is one of the biggest threats that computers and mobile devices face today. It can invade your system without your knowledge, damage important data,
It’s essential to have the right tools when dealing with data recovery. Without the right software, it can be difficult to get back lost information
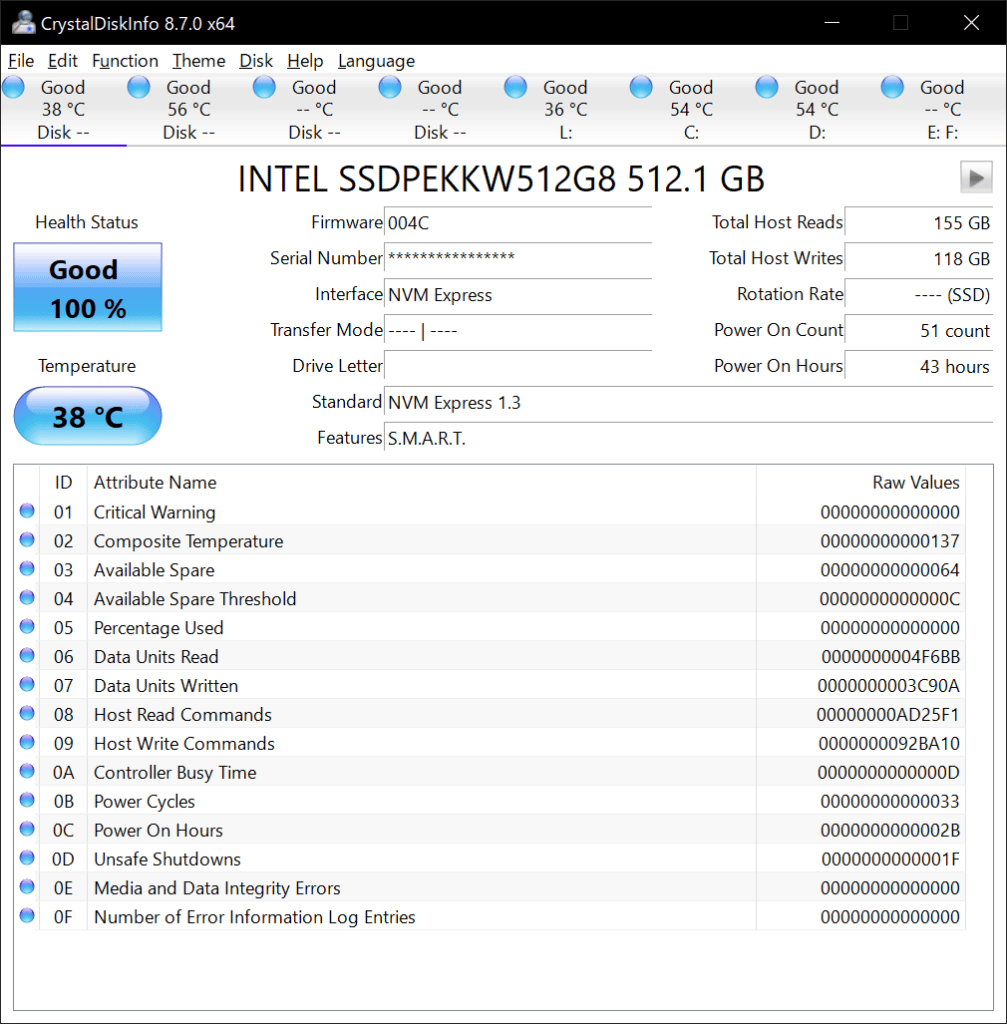
Have you ever experienced a system crash due to challenging drive issues? It can be a frustrating experience, especially if you don’t know how to

In today’s digital age, free software can be found anywhere online. It is an attractive option for those looking to save money on the latest

In recent years, the use of mobile devices has grown exponentially. As the number of mobile users continues to rise, so too has the threat

Malware is a form of malicious software used to disrupt the normal functioning of computer systems. It can steal sensitive information, spread viruses and cause

Fileless malware is a rising cyber threat that has the potential to devastate organisations and individuals alike. A single instance of fileless malware can spread

In today’s digital world, browser extensions are an ordinary and necessary tool for internet users. While they can enhance user experience, specific malicious extensions can

Ransomware is malicious software that has become increasingly prevalent in recent years. It is a type of malware that attempts to extort money from its

Malware is a growing problem affecting computer systems, networks and data. It can exploit vulnerabilities in your system’s firmware, resulting in severe consequences. This article

Online privacy and security are paramount for protecting data and maintaining user anonymity. Using a virtual private network (VPN) is an effective way to ensure

The process of replacing a failing hard drive and transferring data to a new drive can be an intimidating task. Many potential risks are associated

Malicious software, or malware, is a significant threat to computer users today. Viruses, Trojans, worms and other malicious software can cause severe computer damage if

Data is essential for any successful business. It contains the information necessary to make decisions and provide insight into customers, industry trends, finances, and more.

Malware and viruses have become a growing threat to laptop performance in recent years. The effects of these malicious programs can vary from slow system

Data loss can be a devastating event for any individual or business. Without proper backup measures, valuable information and memories can easily be lost forever
Introduction: As we rely more and more on our mobile devices, it’s important to keep them running smoothly. A slow and cluttered device not only

Security researchers have found a new Android banking trojan that can spy and steal information from 153 Android applications. Samsung supplies a range of smartphones
Microsoft has warned about a new strain of mobile ransomware that takes advantage of incoming call notifications and Android’s Home button to lock the device
Systems running the Windows 10 Anniversary Update were protected from 2 exploits even prior to Microsoft had actually provided patches for them, its researchers have

When you’re on the hunt for a new smartphone, it’s likely that you’re focused on cost, style, and includes initially—– and probably not the silicon
The need for virtual private networks has grown exponentially in current times, particularly as individuals spend more time using the internet in their homes throughout

Whether it’s a prying boss or a paranoid partner, no one should snoop on your phone or laptop. But that’s exactly what can happen if