Network issues can be a huge headache, but they don’t have to be. With the right tools and know-how, it’s possible to diagnose and troubleshoot connectivity problems quickly and effectively. Wireshark is one of the best tools for this purpose; it’s an incredibly powerful network protocol analyzer that enables users to see what’s really going on in their networks. In this article, you’ll learn tips and tricks for using Wireshark to diagnose network issues – so you can get back up and running as soon as possible!
We all know how frustrating it can be when our networks fail us; nothing seems to work, from email servers to file transfers. But with Wireshark at your side, you’ll have the upper hand when it comes to troubleshooting these kinds of problems. Wireshark gives you the ability to see exactly what’s going on in your network, so you can identify and solve the issue quickly before any further damage is done.
In this article, we’ll guide you through using Wireshark for diagnosing network issues. We’ll cover topics such as capturing packets, analyzing traffic patterns, filtering data flows, and more. Whether you’re an experienced IT professional or just starting out in networking, this guide will equip you with the skills needed to diagnose and troubleshoot your own connections successfully – so that everyone can stay connected with minimal disruption!
Definition Of Wireshark
Wireshark is an essential, powerful tool for troubleshooting any network issue. It goes beyond the capabilities of any other network analysis tool, offering an unrivalled level of visibility into what’s happening on your network. Its unparalleled versatility allows it to be used in virtually every stage of the diagnosis and resolution process. From detecting and pinpointing problems, to generating reports and automating tasks – Wireshark can do it all!
In addition to its robust feature set, Wireshark also provides an extensive array of customizable options that allow users to tailor their experience to their own unique needs. This means that even novice users can easily get up and running with Wireshark in no time. With its straightforward user interface, anyone can quickly become a master at analyzing networks with Wireshark!
With such vast potential for diagnosing almost any type of network issue, Wireshark has quickly become the go-to solution for IT professionals everywhere. No matter what kind of problem you’re facing, Wireshark is always up to the challenge – making it the perfect choice for addressing any connectivity issues you may be facing. Ready to start exploring how to use Wireshark? Let’s move on to getting an overview of common network connectivity issues next.
Overview Of Network Connectivity Issues
Network connectivity issues can be some of the most frustrating and difficult to diagnose. Whether it’s a basic internet connection issue or something more complicated, understanding the common causes of network issues is the first step to solving them. Let’s take a look at some of the common culprits:
1) Interference: Physical objects such as walls and furniture can impede signal strength and create interference, leading to slow speeds or spotty connections.
2) Poor signal strength: Depending on your geographical location, you may be too far away from a router or access point, resulting in weak signals that are unable to reach their destination.
3) Faulty hardware: Sometimes network issues can be caused by faulty hardware, such as damaged cables or outdated routers that cannot keep up with modern speeds.
The key to successfully troubleshooting any network issue is being able to identify which one of these is causing the problem – and that’s where Wireshark comes in. By capturing packets with Wireshark, you can get an inside view of what’s happening on your network and quickly pinpoint the source of any connectivity problems. Let’s take a look next at how capturing packets with Wireshark works!
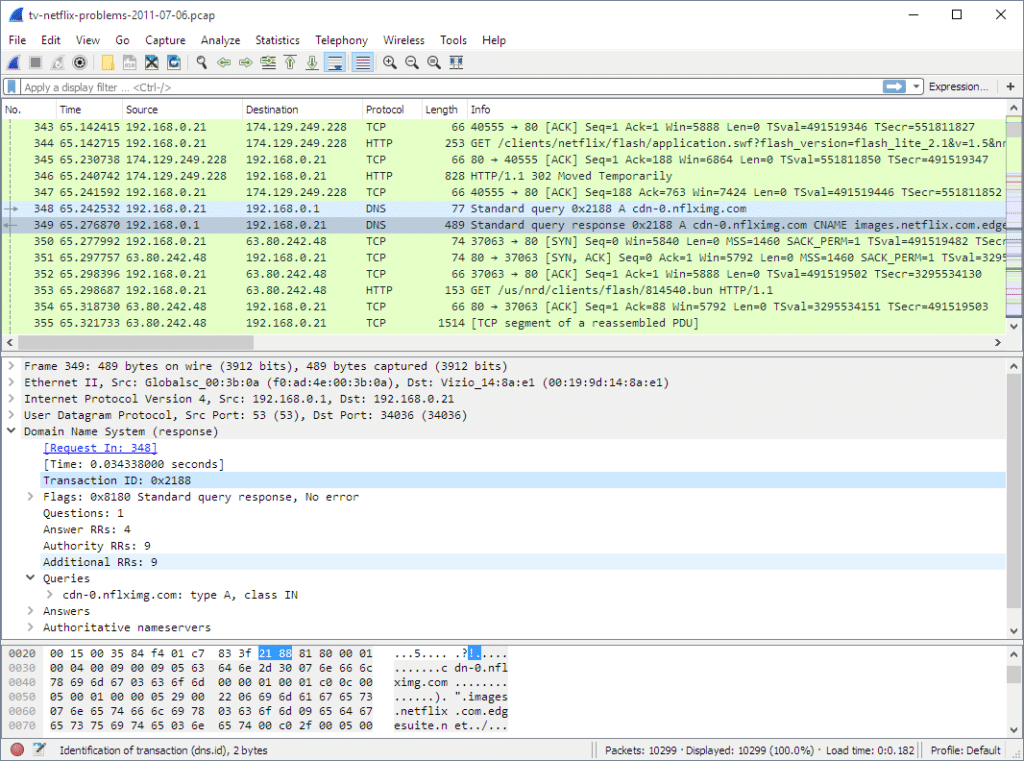
Capturing Packets With Wireshark
Welcome to the world of packet capture! If you want to get to the bottom of network issues, Wireshark is your go-to tool. This powerful protocol analyzer can help you diagnose a wide range of problems, from slow connections to packet loss and latency issues. Here’s a quick guide on how to get started:
1) Download and install Wireshark: The first step is to download and install Wireshark onto your computer. Once it’s installed, you’ll be ready to start capturing packets.
2) Choose an interface: You’ll need to select which interface you want to capture packets from. Depending on your network setup, you may need multiple interfaces for capture.
3) Start capturing packets: Now that everything is set up, simply click the “Start” button in Wireshark and start collecting data.
4) Filter for relevant data: To keep the data manageable, you can use filters to narrow down the types of packets you’re looking for.
5) Analyze captured data: Once all the data has been collected, it’s time to analyze it and look for any patterns or anomalies.
Now that we’ve got a basic understanding of how Wireshark works, let’s dig deeper into how you can use it to analyze network traffic and identify potential problems!
Analyzing Network Traffic With Wireshark
Now that we have some data to work with, it’s time to start analyzing it. With Wireshark, you can look at the different packets that are being sent and received on your network in order to identify any potential issues. You can also use the filters in Wireshark to narrow down the specific types of packets you’re looking for, making it easier to spot anomalies.
When using Wireshark for troubleshooting, there are a few key things to look out for. Firstly, keep an eye out for packet loss or corruptions. This could indicate issues with your hardware or software configuration. Secondly, pay attention to latency levels between devices on the same network – if one device is experiencing high latency compared to others, this could be a sign of congestion or a faulty connection. Lastly, check whether certain protocols are being blocked – this could mean that something is preventing these protocols from functioning properly.
By utilizing these tips and tricks when troubleshooting networks issues with Wireshark, you’ll be able to quickly pinpoint any underlying problems and get your network back up and running in no time!
Filtering Packets With Wireshark
When it comes to diagnosing network issues, Wireshark is one of the most powerful tools at our disposal. It can help us identify potential problems with our networks and even provide us with information about what data is being sent and received. With its filtering capabilities, we can find out exactly what type of packets are being sent and received, allowing us to detect any anomalies that could be causing connectivity issues.
Using Wireshark, we can quickly filter out unnecessary packets and narrow down our search to only those that are relevant to our network. This makes it much easier to spot any potential issues with the protocol or hardware configurations that might be causing the problem. Additionally, by filtering specific protocols or ports, we can also see if anything is preventing certain services from functioning correctly.
By harnessing all of these features in Wireshark, we’re able to diagnose and troubleshoot common network issues more efficiently than ever before. Armed with this knowledge, we can start implementing solutions that will get our networks back up and running as soon as possible. Now let’s take a look at how we can use Wireshark to troubleshoot firewall issues next!
Troubleshooting Firewall Issues
In order to properly diagnose network issues, we need to be able to identify and troubleshoot any problems relating to firewalls. Firewalls are used to restrict access to certain services or networks for security reasons, but if they’re not configured correctly, they can cause major connectivity problems. To ensure that your firewall is working correctly, it’s important to understand the different types of firewalls and how they work.
The most common type of firewall is a packet-filtering firewall, which works by examining each individual data packet as it passes through the network and deciding whether or not it should be allowed through. If a packet matches certain criteria, then it will be allowed to pass through; otherwise, it will be blocked. This type of firewall can help protect against malicious attacks, as well as prevent unauthorised access to certain areas of the network.
To ensure that your packet-filtering firewall is functioning correctly, you’ll need to configure the ruleset correctly so that only authorised packets are allowed through. You’ll also want to monitor your logs regularly for any suspicious activity and make sure that you have adequate security measures in place for all of your systems. By taking these steps and ensuring that your firewall is properly configured, you’ll be able to minimize the risk of connectivity issues due to firewalls.
Armed with this knowledge about how firewalls work and how we can troubleshoot them, let’s take a look at how we can use Wireshark for local area network (LAN) analysis next!
Local Area Network Analysis
With an understanding of firewalls, we can now delve into the world of local area network analysis with Wireshark. This powerful tool can provide a wealth of information about our networks, allowing us to identify and troubleshoot any issues quickly and easily.
First, let’s start by looking at how Wireshark captures packets from the network. When Wireshark is running, it will capture all packets that pass through your network interface card (NIC), regardless of whether they’re sent or received. This allows us to monitor all traffic passing over the network, giving us an in-depth view of exactly what is happening on our networks. With this data, we can quickly identify any problems that are occurring on our LANs.
Next, let’s discuss how Wireshark can be used to interpret IP addresses and ports. Every packet that is transmitted across the network contains both an IP address and a port number which identifies the sender and recipient of the data. By examining these values in each packet, we can determine which systems are communicating with each other and where any potential problems may be occurring in our networks. This gives us valuable insight into our LANs so that we can quickly diagnose any issues that arise.
By combining our firewall knowledge and analyzing data with Wireshark, we have a comprehensive toolkit for efficiently and effectively diagnosing network issues. Now let’s take a look at how we can interpret IP addresses and ports to gain further insights into our networks!
Interpreting Ip Addresses And Ports
Interpreting IP addresses and ports are key to understanding how our networks communicate. With Wireshark, we can easily identify which systems are communicating with each other and pinpoint any potential issues that may be present. Here are the steps we should take when analyzing packets with Wireshark:
- Identify the source IP address of each packet. This will tell us where the data is coming from in our network.
- Examine the destination port for each packet. This will help us determine which system is receiving the data and if there are any potential problems with communication between systems.
- Look at the protocol type of each packet to understand how networks communicate with each other (e.g., TCP or UDP). We can also check for any discrepancies between what protocols our systems are set up to use and what they are actually using on the network.
- Analyze the headers of each packet to get a better understanding of where problems might be occurring in our networks, such as dropped packets or an incorrect port number being used by one system over another.
By understanding these four steps, we can quickly analyze our network traffic and diagnose any issues that may be present in our LANs. Armed with this knowledge, let’s move on to examining protocols and packet headers to gain further insight into our networks!
Examining Protocols And Packet Headers
Now that we’ve covered the basics of interpreting IP addresses and ports, let’s take a deeper look into protocols and packet headers. By understanding these components of network communication, we can better diagnose issues that may be occurring in our networks. Here are five key elements to consider when analyzing protocols and packet headers:
- Data payloads – Looking at the data payloads for each packet can help us determine if any data is being lost or corrupted during transmission.
- Retransmissions – Examining how often retransmissions occur will help us identify any potential problems with our network connections.
- Error messages – Error messages can provide insight into what might be causing issues with our network connections, such as incorrect port numbers or protocol violations.
- Time stamps – Time stamps allow us to track how long it takes for packets to travel across our networks and pinpoint where any potential delays might be occurring in our networks.
- Routes & hops – Analyzing routes and hops can help us determine if there are any points of congestion on our networks which could be impacting performance issues or causing latency problems.
By taking the time to analyze these five elements, we can get a more thorough picture of what’s going on within our networks and quickly isolate any potential problems that may be present. With this information in hand, we’re ready to move on to tracing connections with time stamps!
Tracing Connections With Time Stamps
Uncovering network issues often requires us to trace connections through time stamps. By understanding how our packet data is traveling, we can quickly identify any potential problems that may be occurring in the network. Let’s take a closer look at how we can use this technique to pinpoint the source of connectivity issues.
The process of tracing connections with time stamps begins by looking at the timestamp on each packet. This will tell us how long it has taken for the packet to travel from point A to point B and will allow us to determine where any potential delays might be occurring in our networks. We can also compare these time stamps against what is known as a baseline, which is a reference point that allows us to measure performance against a standard.
By tracking these timestamps over time, we can get an idea of how well our network is performing and whether or not there are any underlying issues that need addressing. For example, if we notice that our network performance has suddenly dropped off, then this could indicate that something is amiss and further investigation may be needed. With this valuable information in hand, we’re now ready to move on to detecting malicious activity!
Detecting Malicious Activity
Detecting malicious activity on our networks is a critical step in ensuring the security of our systems. To do this effectively, we must first understand how to identify and analyze suspicious behavior.
Firstly, it’s important to keep an eye out for any unexpected traffic or changes in data communications. This includes checking for large amounts of data being transferred, as well as any suspicious IP addresses that may be sending or receiving information. Additionally, we should also look at any connection requests that are coming from outside our network and make sure they are legitimate.
Secondly, be sure to monitor user behavior on the network. This means looking out for anything unusual such as frequent web surfing activity or excessive downloads that could indicate malicious activity is taking place. Also pay close attention to any changes in user accounts, such as new accounts being created or passwords being reset without authorization.
Thirdly, it’s essential to review system logs regularly for signs of intrusion attempts or other anomalous events. By doing this we can gain valuable insight into what is happening on our networks and spot potential threats before they become a serious problem.
From here we can use the knowledge obtained from our investigations to take action against malicious actors and protect ourselves from future attacks. With these steps taken, we can move on to the next stage: generating reports for IT teams so they can further analyze the situation and address any issues accordingly.
Generating Reports For It Teams
Once we have identified suspicious activity, the next step is to generate reports for IT teams so they can further analyze the situation and address any issues accordingly. To do this effectively, it’s important to include as much detail as possible in our reports in order to provide a complete overview of the issue.
When creating these reports, there are several key components that should be included:
• Technical Details: This includes an analysis of the data traffic on the network as well as any potential malicious activities that were detected. It’s also important to include information about any software or hardware that was affected by the attack.
• Remediation Steps: We should also provide recommendations on how to mitigate and prevent future attacks from occurring. This may include making changes to user accounts and passwords, updating antivirus software, or implementing additional security measures such as firewalls and encryption protocols.
• Supporting Evidence: Finally, it’s important to provide evidence to back up our claims, such as screenshots of logs or other relevant documents. This will help IT teams understand the scope of the problem and take appropriate action in a timely manner.
By including all of this information in our reports, we can ensure that IT teams are able to identify and address network anomalies quickly and efficiently – leading us into our next section on preventing network anomalies.
Preventing Network Anomalies
Nowadays, it is more important than ever to ensure that our networks are protected against malicious attacks and anomalies. To do this, we must take proactive steps to prevent these issues from occurring in the first place. In this section, we’ll explore some of the most effective strategies for preventing network anomalies and keeping our systems safe.
First, we should prioritize implementing strong security measures such as firewalls, encryption protocols, and user authentication. This will help protect against unauthorized access to our systems and reduce the risk of data breaches. We should also regularly update antivirus software and other security applications to ensure they are up-to-date with the latest threats. Additionally, having a comprehensive backup system in place is essential for restoring any lost or damaged data quickly and efficiently.
Finally, it’s essential that all users understand their role in protecting the network from potential attacks. This means educating them on best practices such as creating strong passwords, avoiding suspicious websites or links, and recognizing phishing emails or other potential scams. By helping everyone understand their part in maintaining a secure environment, we can drastically reduce the chances of experiencing any malicious activity on our networks.
As we’ve seen here today, there are many ways to proactively protect our networks from anomalies – now let’s look at how we can optimize performance utilizing Wireshark.
Optimizing Performance Utilizing Wireshark
In order to get the most out of our networks, it is essential that we optimize their performance. Wireshark is a powerful tool for diagnosing and troubleshooting network issues, allowing us to identify slowdowns, bottlenecking, and other problems. Let’s explore how we can use this versatile program to its fullest potential:
• Analyzing Traffic:
Wireshark can help us analyze data packets traveling across the network. By studying packet headers and other information, we can identify any anomalies or errors in the traffic flow. This will allow us to pinpoint exactly where a problem may be occurring and address it before it becomes an issue.
• Troubleshooting Connectivity Problems:
When dealing with connectivity issues, Wireshark can be used to trace back the source of the problem. We can run basic tests such as pings and traceroutes to check for latency issues or DNS resolution problems. Additionally, Wireshark allows us to filter out unnecessary traffic so that we can focus on the relevant data and quickly diagnose any issues that may be present.
By utilizing these tips and tricks for using Wireshark for diagnosing network issues, we can ensure that our networks are running optimally at all times – no matter what challenges come our way. Now let’s turn our attention to some important security considerations when using this powerful program.
Security Considerations
Now that we have discussed the many ways Wireshark can help us diagnose and troubleshoot network issues, let’s turn our attention to security considerations. When using this powerful program, we must be mindful of the potential risks and make sure that we are taking all necessary steps to protect ourselves and our data from malicious actors.
First and foremost, it is important to remember that Wireshark requires access to sensitive information in order to do its job. As such, it is essential that only users who have been granted explicit permission by their system administrators – or other authorized personnel – be allowed to use it. Additionally, all users should be properly trained on how to safely use the program and make sure that they are aware of any security protocols or policies in place at their organization.
Finally, we must always keep our systems up-to-date with the latest patches and security fixes. This will help ensure that our networks remain secure against any potential threats or vulnerabilities. By taking these simple yet effective precautions, we can use Wireshark more confidently knowing that our data is safe from harm.
Frequently Asked Questions
What Is The Cost Of Wireshark?
The cost of Wireshark is not as high as one might think. It’s actually quite affordable, and it can be downloaded for free from the official website. In fact, it could be said that this powerful network analysis tool is a steal for any IT professional or network administrator.
Using Wireshark to troubleshoot connectivity issues is like having a crystal ball. It can help you pinpoint the exact source of the problem and get your network running smoothly again in no time. The cost may seem trivial when compared to the value of being able to quickly diagnose and resolve any issue that arises.
It’s easy to get caught up in the details when trying to diagnose a problem, but with Wireshark you can cut through the clutter and focus on what matters most: getting your network back up and running as soon as possible. By leveraging its powerful features, you can get right to the root of the issue and start taking steps towards a resolution quickly and efficiently.
Wireshark offers an invaluable resource for those in need of assistance with their networks. With its extensive capabilities, it’s no wonder why it’s become such a popular choice among tech-savvy professionals looking to troubleshoot connectivity problems. Best of all, anyone can get started with just a few clicks of their mouse – making it well worth every penny!
Is Wireshark Compatible With All Operating Systems?
Wireshark is a network protocol analyzer that’s been used by IT professionals for years to diagnose and troubleshoot network-related issues. But many people wonder if it’s compatible with all operating systems.
The short answer is yes, Wireshark is compatible with all major operating systems, including Windows, macOS, Linux and Unix. It also offers support for Android and iOS devices, so you can analyze your networks on the go. You don’t need to worry about compatibility when using Wireshark for troubleshooting connectivity problems.
Plus, Wireshark is free and open-source software that’s constantly updated to improve its performance and provide the best possible results. This means you don’t need to spend money on expensive tools or dedicated hardware – simply download Wireshark from their website and get started diagnosing your network issues.
TIP: To get the most out of your Wireshark experience, read up on some of the helpful tutorials available online so you know how to use its features properly. With a bit of practice, you’ll be able to easily identify and resolve any potential connectivity problems in no time!
Can Wireshark Be Used For Remote Network Analysis?
Did you know that Wireshark is used by over 500,000 people around the world? This powerful tool not only helps with local network analysis and diagnostics, but also has the capability to be used for remote networks.
The great thing about Wireshark is that it can be used for both wired and wireless networks, regardless of the operating system. It can easily detect problems related to network connectivity such as congestion on the network or packet loss due to lack of bandwidth. With this information, it can help diagnose the cause of any issues, allowing users to narrow down their troubleshooting efforts quickly and efficiently.
Thanks to its wide range of features and compatibility with many devices, Wireshark can be a great asset when troubleshooting connectivity problems remotely. From capturing packets to analyzing traffic, Wireshark provides valuable insights into what’s happening on the network in real-time. This makes it an invaluable resource for IT professionals who are looking to identify and resolve any potential problems quickly.
Whether you’re new to network analysis or a seasoned professional, Wireshark can provide you with the tools needed to diagnose and solve complex networking issues from afar. With its comprehensive suite of features and cross-platform compatibility, it’s no wonder why so many users rely on this powerful program for their remote networking needs!
Is There A Wireshark Certification Available?
When it comes to network analysis, Wireshark is one of the most popular and widely used tools. The open-source application can be used to troubleshoot connectivity issues and diagnose network issues, but many people want to know if there is a Wireshark certification available.
It’s true that there are certifications out there for those interested in demonstrating their knowledge of Wireshark. Here’s what you need to know:
- The official certification is called WCNA (Wireshark Certified Network Analyst). It’s an online exam that tests your knowledge of how to use Wireshark for packet analysis and troubleshooting networking problems.
- The exam consists of multiple choice questions as well as practical exercises in which you will be asked to identify the cause of a problem from a packet capture file provided by the examiner.
- You must answer at least 70% of the questions correctly in order to pass and receive the certification, so it’s important to study up before sitting for the exam.
Studying for this type of certification takes dedication and commitment, as there is quite a bit of material to cover when it comes to using Wireshark for packet analysis and troubleshooting networking problems. Fortunately, there are numerous resources available online that can help you prepare for the WCNA exam, including practice exams, tutorials, and sample capture files. With enough preparation, anyone can become certified in using this powerful tool!
How Does Wireshark Compare To Other Network Analysis Tools?
Troubleshooting connectivity issues can be like trying to find a needle in an ever-growing haystack. But the right tools can make all the difference, and when it comes to network analysis, Wireshark is one of the top contenders. Let’s look at how this powerful tool compares to other solutions available today.
To understand why Wireshark is so popular with network administrators, it helps to look at what sets it apart from its competition. For starters, Wireshark has a wide range of features designed to capture and analyze data packets over any network protocol. It also offers advanced packet filtering capabilities that allow users to quickly narrow down their search for root cause issues. And because Wireshark is open source and free, it’s accessible to almost anyone who needs a reliable network analysis tool.
But Wireshark isn’t the only player in this arena; there are plenty of other solutions out there too. Some of these offer more sophisticated features than Wireshark, such as deep packet inspection or more detailed analytics capabilities. They may also come with a price tag attached, making them less accessible for smaller businesses or those on tighter budgets.
In any case, finding the right solution depends on understanding your particular environment and needs — and being willing to do some research into which tool will work best for you. With this in mind, it pays off to explore all your options carefully before deciding on the best fit for your organization’s networking needs.
Conclusion
The cost of Wireshark is relatively low and it’s compatible with most operating systems, making it a great choice for many users. Furthermore, it can be used for remote network analysis, although there is no official certification available. When compared to other network analysis tools, Wireshark has a lot of features and capabilities that make it an excellent option.
When diagnosing network issues, using Wireshark can help you find the source of the problem quickly and efficiently. It’s important to understand how to use the tool effectively so that you can get the best results. By learning tips and tricks for troubleshooting connectivity problems with Wireshark, you’ll be able to identify problems more accurately and address them quickly.
So why not take advantage of this powerful tool? With its wide range of features and benefits, leveraging Wireshark when troubleshooting network issues could prove invaluable in keeping your networks running smoothly. What are you waiting for? Get started with Wireshark today!












